This Blog walks you through setting up Single Sign On (SSO) for an Identity provider with Salesforce Marketing Cloud as a Service Provider. The following guidance helps with the specifics of implementing SSO alongside our existing
Marketing Cloud supports identity providers that use the SAML 2.0 specification, such as Salesforce Identity, Shibboleth, PingFederate, and Active Directory Federation Services (ADFS). The configuration for the identity provider must trust the Marketing Cloud product as a service provider, sometimes called a relying party.
1. Enable SSO
a) Enable SSO on your Salesforce Marketing Cloud Account. SSO could already be enabled on the Enterprise account. To verify, log on to the Main Enterprise account Id on your MC instance and then go to Setup > Administration > Data Management > Key Management.b) If SSO is enabled, the SSO Metadata radio button appears. If the radio-button doesn’t appear in the UI, then either SSO isn’t enabled or you are within a Business Unit. If you are on the Enterprise-level business unit and SSO isn’t enabled, raise a case to have support enable SSO for your account.
NOTE: You can only have one active SSO Metadata active at a time.
2. Retrieve SAML Metadata
After SSO has been enabled, you must retrieve your SAML Metadata from the MC account. It’s located under Setup > Settings > Security > Security Settings > Single Sign-On Settings > SSO SAML Metadata (Button) A url looks similar to the following:
https://TenantSpecificEndpoint.login.exacttarget.com/SFMCMetadata
NOTE: If you have an option to select a certificate version to choose the one with the latest expiration data example (Jan 2021 – mc.login.exacttarget.com (expires February 5, 2022))
3. Apply to your IDP
You now must apply the SFMC Metadata to your IDP.
4. Create Key
After the SFMC Metadata has been applied, you’ll then take the metadata from your IDP and input it into the Key Management section of SFDC. Within your Org go to Setup > Administration > Data Management > Key Management. Click the Create Button then select SAML_SSO Metadata A <NameIDFormat> Value is required the IDP Metadata entered into the SFMC configuration add one of the following lines to the metadata if you receive an error saying the <NameIDFormat> is missing or invalid. If the <NameIDFormat> is in the wrong location it will also error.
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</md:NameIDFormat> <md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat> <md:NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:persistent</md:NameIDFormat> <md:NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:entity</md:NameIDFormat>
The <NameIdFormat> must be placed in between the </KeyDescriptor> closing tag and the <SingleSignOnService> Open tag.
</md:KeyDescriptor>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:persistent</md:NameIDFormat>
<md:NameIDFormat>urn:oasis:names:tc:SAML:2.0:nameid-format:entity</md:NameIDFormat>
<md:SingleSignOnService ... >
NOTE: the MD: is an XML namespace, and if you IDP Metadata doesn’t use it or it’s different, you must remove or change it accordingly. The <NameIDFormat> opening and closing tags must match the name space used in the closing <KeyDescriptor> and opening <SingleSignOnService> elements.
5. Save Key
Now hit Save, if the key is accepted, a green banner appears and the Key was saved successfully. If an error occurs, and you can’t resolve the issue, then open a Support Case.
6. Enable SSO Setting
After you have a green banner and a key in place, You must enable SSO for your MC account under Setup > Settings > Security > Security Settings > Edit > Single Sign-On Settings > Enable SSO by selecting or checking the setting and then selecting Save.
NOTE: SFMC requires MFA to be enabled on SSO connections by the 2022 deadline. We recommend it to be introduced prior for a more secure experience.
NOTE: Certificate version may vary or there may be multiple versions listed.
7. Configure User SSO Settings
The next step will be to go to Setup > Users > Users, then click a User. Select the enable SSO option and add the Federation ID that was configured on the IDP side. If the value is unknown, you must verify with your IDP or IT team to gather that information to continue.
NOTE: A common situation with SSO enablement is the End-User attempting to log in can’t reset their user password or login via the mc.exactarget.com URL. The user and pass log in route is ignored when SSO is enabled. This is functioning as designed as an End-User is only able to log in via the SP initiated link provided under Setup > Settings > Security > Security Settings > Edit > Single Sign-On Settings > Marketing Cloud SP Initiated Link, or an IDP initiated connection via a dashboard or another method to start the conversation. ALL mc.exacttarget.com requests are received but not processed for any user that has the SSO Enabled box enabled. If a user is not SSO enabled then this issue will not present and they can request password normally.
8. Test the SSO Configuration
Test the newly appointed SSO user, either via an incognito window or a freshly purged cache browser. If you receive an error, open a case with support. If you log in without issue you can go ahead and implement further SSO users.
BestPractice: Leave at least one admin user not on SSO so you can recover the account and login to the SFMC to correct any configuration SSO issue.
Troubleshooting tips
SSO No FederationID
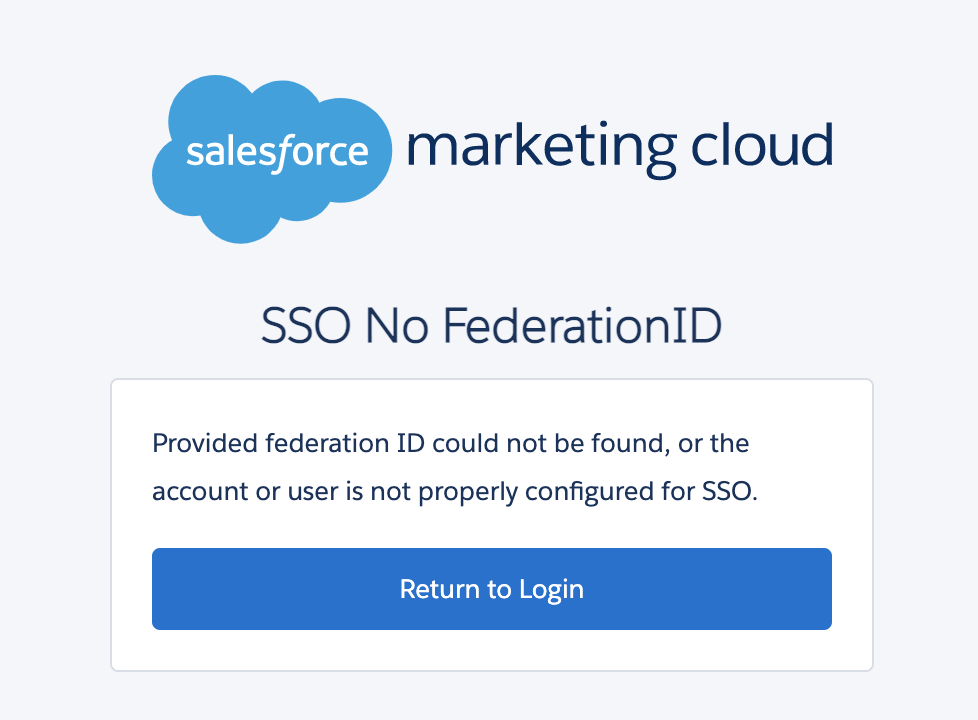
Resolution:
Go to Marketing Cloud account –> Login with your user details –> Click on Setup –> Manage users –> Select the user who are facing this issue –> click on the user –> Click on enable SSO checkbox –> Enter Federation ID as “employee ID or email id” as per your IDP setup.
SSO Fatal Profile Error
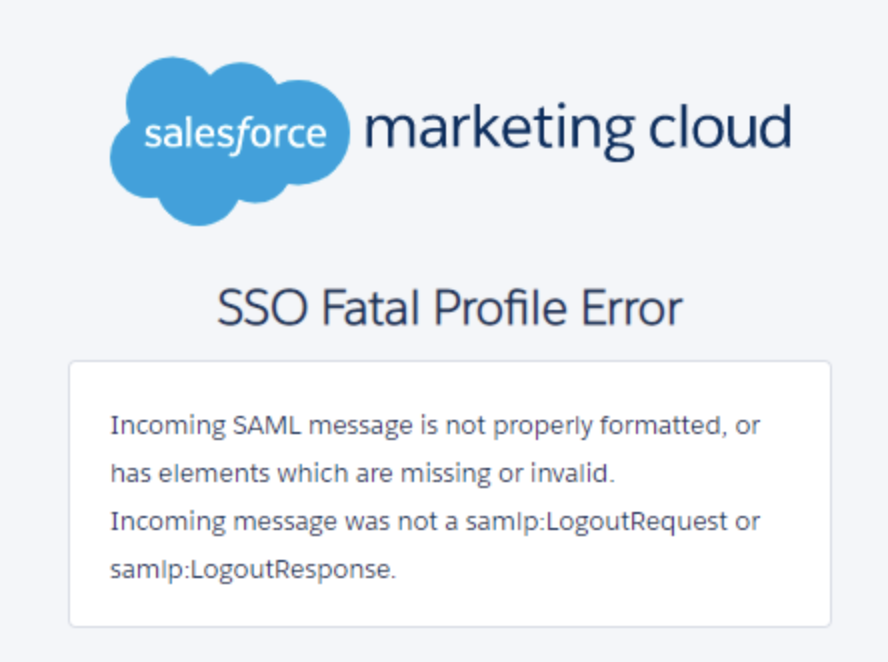
Resolution:
The root cause of the above screenshot was an improper value included in the ACS URL on the Okta side of the prebuilt configuration. The SLO link was used in place of the ACS link. This caused the SP to validate the Logout request when the request was a login request throwing the error.
The second error was caused but using the RequestInitiator Link in the ACS link. That should have been caught by me, but it was not.
The proper link to use would look like this in the Metadata
<md:AssertionConsumerService Binding=”urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST” Location=”https://mcsn4g-xxxxxxxxxxxxxxx.login.exacttarget.com/Shibboleth.sso/SAML2/POST” index=”1″/>
This value is what corrected the issue. https://mcsn4g-xxxxxxxxxxxxxxxxxxxxxxx.login.exacttarget.com/Shibboleth.sso/SAML2/POST
Single Sign on Certificate
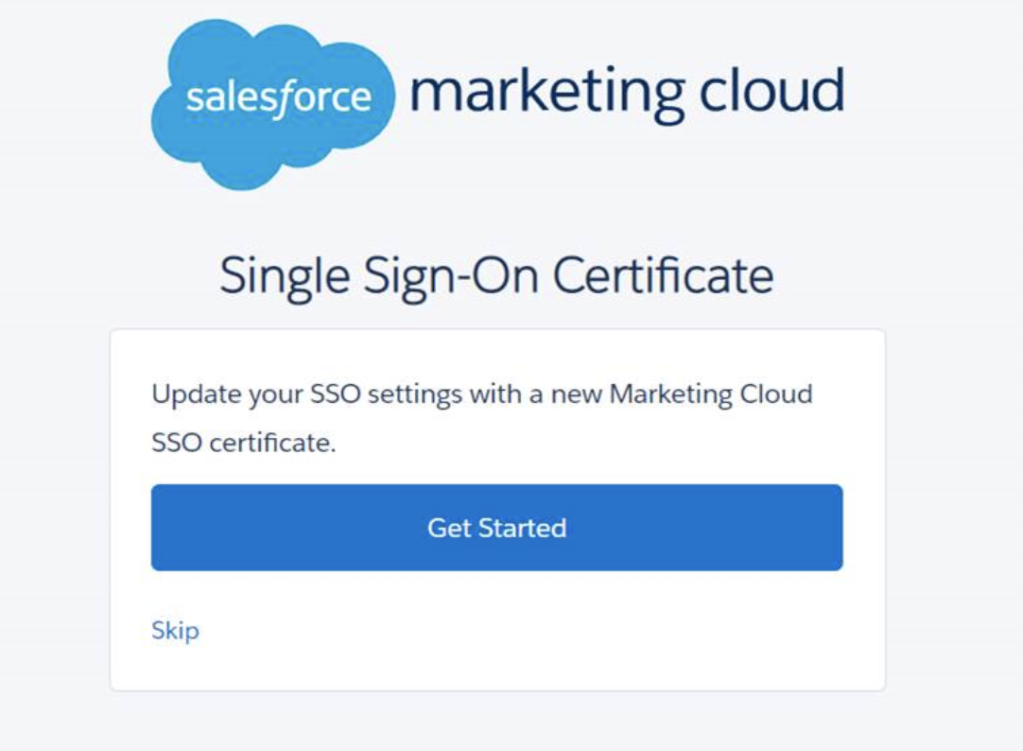
Resolution:
SFMC is integrated with Azure for SSO which has been working fine, Recently when i try to login, SFMC prompting a message that i need to update SSO certificate which i have to take from SFMC Metadata. Problem is SFMC Metadata simply gave the key for .cert format…but our Azure is expecting .pfx file…Also to convert .cert to .pfx…it needs private key and password as well… so where do i need to get them.
SFMC Notice https://help.salesforce.com/articleView?id=sf.mc_rn_october_2020_platform_sso.htm&type=5
Steps to update https://help.salesforce.com/articleView?id=000356220&type=1&mode=1
Invalid Assertion
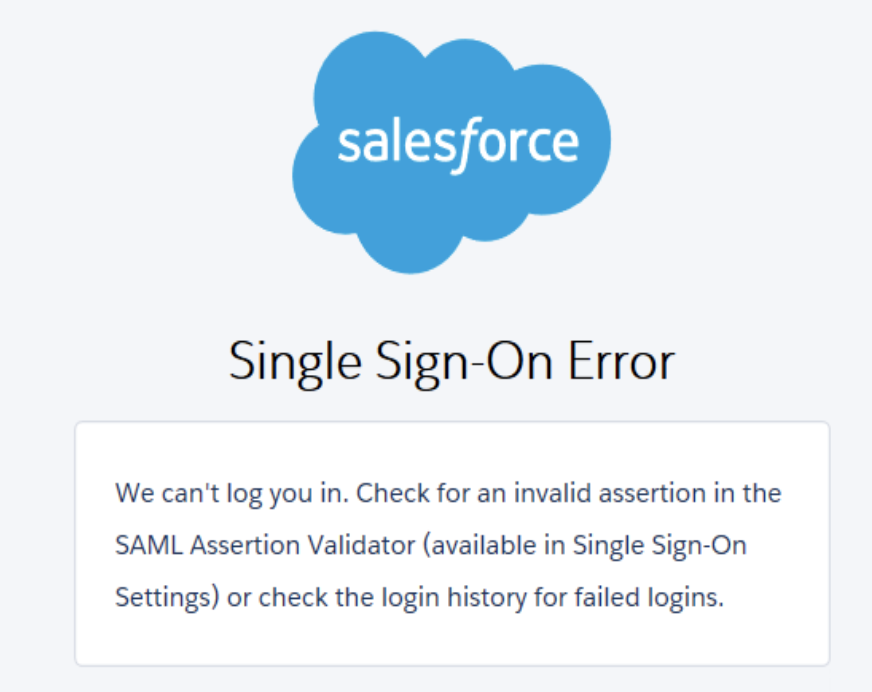
Looks like, the Fed ID was correct. The problem ended up being SAML Type was set to Assertion Contains the User’s Salesforce username. changed it to the second option Assertion contains the Federation IS from the User Object.
Ref: https://www.linkedin.com/pulse/setting-up-sso-salesforce-marketing-cloud-petr-svestka-/


I had the SSO No FederationID when switching from on-premise ADFS to Azure. I ended up having to uncheck the enable sso on each user, save, check it again, and save. IDK why, but MC is crazy like that sometimes.
I had the SSO No FederationID when switching from on-premise ADFS to Azure. I ended up having to uncheck the enable sso on each user, save, check it again, and save. IDK why, but MC is crazy like that sometimes.
Hi Ben, I believe, it’s with session enablement, page didn’t refresh properly that causes save functionality.